EXTINCTION LEVEL EVENT: How to avoid a single, and potentially fatal, Strike
What is true "security perimeter" of business leaders, company bank accounts, and the investor capital within? Read some real world experience in the year that security, and scams, changed.
The Three Strikes Theory states that companies, irrespective of size or type, are only ever three strikes away from success or disaster… but sometimes there can be a single extinction-level strike.
Significant advancements in AI and technology over the past 12 months have drastically changed the risk landscape - and I want to share with you an extinction-level event that recently happened to me, so that you can review your own risks that may need to change based on these major technological shifts.
2023 was the year of data breaches. In 2024 cybercrime is on the rise, aided by AI voice recognition, replication, and deep fake technology. The risk of identity theft and compromised bank accounts grows. What would happen to your business if someone gained access and stole every dollar you have, or every dollar your investors put in? Would you be out of business, today, in a single strike?
Three Strikes Theory is about sharing real life case studies and implementable insights.
If you don’t have much time, you can watch/listen to the 6 minute interview or just read the key action points below. It might just save your business from a single, and potentially fatal, strike.
Below is my real life experience when my identify was stolen, my bank account compromised, and the funds in those banks accounts put at risk. It happened in the blink of an eye, and all the risk mitigations I thought I’d covered, were very quickly erased. I’m sharing this to give you context and I have interviewed two industry experts to share insights that are quick and easy to understand and implement.
Real life context - my identity was stolen and my back account compromised:
- I was the victim of identity theft on 23 December at 7:30pm.
- Someone called Commonwealth Bank, impersonated me and got through enough security layers to add their mobile number to my Netbank profile (no doubt the consequence of many years worth of password and security hacks paying off)
- It highlighted the importance of two-factor authentication as the last line of defence, and how flimsy SMS verification can be. (Watch/listen/read this 6 minute interview with Nigel Phair, one of Australia’s leading cyber security experts)
- I picked it up on the morning of 24th December (Christmas Eve) because of an automated SMS from the bank stating “a new mobile number has been added to your account”. The timing of this hack was smart, because I could easily have ignored it at a time like this ,or could simply have been unavailable.
- I spent an hour on hold, spoke to the fraud department for five minutes, then on hold for another 20 minutes.
- They told me to call Apple and go through a full security check with them to make sure there was no nefarious software running on my phone or computer (a much shorter hold experience and a guided “Safety Check” - you can have a look in Settings> Privacy & Security > Safety Check and run it yourself, right now).
- Once the bank determined there had been fraud, my entire bank profile was locked down, and I had to wait to go into branch in-person and physically ID myself with passports to reopen it.
- A full investigation was launched, including an internal review of the bank employee who handled the call (in case they were in on it)
- I used GoogleOne for a Dark Web Report (only available for personal email addresses apparently) see screenshot below of my personal data available for sale on the Dark Web, right now.
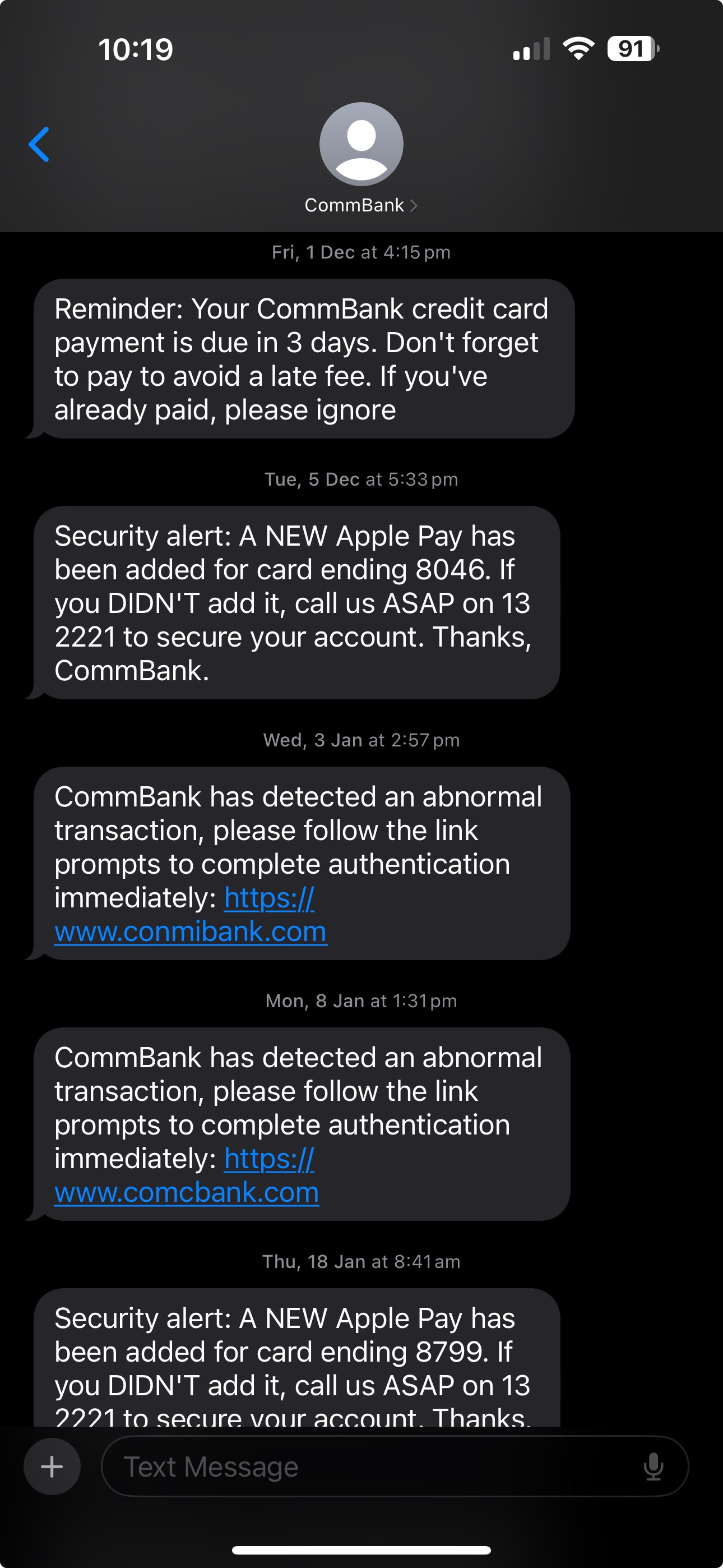
The SMS notifications I receive from Commonwealth Bank are all from “CommBank” in my phone.. BUT on the same message stream I also started receiving SMS that were clearly spam.. HOW!?! (see screenshot)
Interview with Alex MacPherson, CEO of Kudosity
To try to understand what on earth was going on, I had a coffee with Alex MacPherson, the CEO of Kudosity - a conversational AI / messaging / SMS business which 35,000+ companies around the world use to engage with their customers. If anyone would know about SMS/Messaging fraud, and how to prevent it, it would be Alex.. and this is what he told me:
“...across the telco messaging ecosystem globally, the “FROM” field is technically speaking, FREE TYPE. While laws of the land generally say otherwise, the reality is that , if you have access, you can impersonate anyone or any business you like using the "from field", hence the attraction of fraudsters and spammers to get said access! The regulation and policing in this space has picked up pace in recent years, but had remained very underwhelming in a lot of jurisdictions for many years. So the job of consumer protection has fallen to ecosystem service providers platforms like ours to put appropriate safeguards in place in front of any connectivity into the telco's. But the scammers and fraudsters are no less active on the provider side seeking access, as they are the retail side when they gain access. The initiatives like a Sender ID registry pending in Australia will go some further ways to preventing such frauds from taking place and are a long overdue important next step in ensuring a safe, useful and flourishing business to consumer messaging ecosystem”
When I asked Alex around how he managed this in his business he said:
“We’ve always tried to be ahead of the curve on fraud like this, and have built tech, systems and processes that are what we consider to be best practice in verification and compliance - but the reality is that people and businesses get scammed all the time, and fraudsters occasionally find a way through.”
Alex then shared a story around SMS fraud which I found fascinating.. and dispelled the myth that all fraud is technically sophisticated, it involved a single guy in the suburbs with a SIM card “farm”.. you can read about that story here.
Do you have a story to share with me?
Interview with Nigel Phair, cyber security expert
To understand the risks and get some actionable advice around what to actually do about them I interviewed Nigel Phair. He’s quite the guy, a Professor at Monash University, published author of Cybercrime: The Reality of the Threat, Chair of CREST Australasia, Chair of the .au domain administrator, and the go-to guy for news media on all things cybercrime. I figured he’d know what was up.
Nigel’s number one piece of advice he believes everyone needs to realise and do, today, to protect themselves:
Multi-Factor Authentication (MFA) is crucial, is our last line of defence, but not all MFA methods are equal.
POOR MFA
SMS-Based
Email-Based
GOOD MFA
Push Notification: sent to a trusted device (often through an app that has ben logged into using facial recognition), which the user acknowledges or approves for access. Apple and Commonwealth Bank increasingly use this as a method of verification when you’re on the phone with them.
BEST MFA
Biometric Authentication: facial resignation, because it’s frictionless
App-Based Authentication: because it’s a new code every few seconds
Hardware Tokens: like a USB dongle or a key fob that generate a new code at fixed intervals
Nigel’s three areas of security advice:
Three main areas for enhancing personal and financial security:
- Be Cautious with Personal Information: (Duh? But how..)
- Recognise the significance of your identity attributes and be mindful of the information shared online, especially on social media.
- Understand that details like your mother's maiden name, schools attended, property purchased, photos of your first car etc, can all be gathered and exploited by criminals.
- Implement Strong Multi-Factor Authentication (MFA): Turns out SMS is the crappiest 2FA/MFA
- Realise the importance of using robust MFA methods, particularly app-based solutions that offer facial recognition, over weaker forms like SMS-based authentication.
- Regular Data Backup and Software Updates:
- Ensure automatic updates are enabled for all software to immediately patch vulnerabilities and keep security measures up to date.
- Use an external device for cold backup storage and regularly save data then disconnect from your main device them to protect against cyber threats. (Be honest, who among us does this? Maybe I need to consider this.. hmm..)
The significant changes in technology advancements will rapidly advance the risks we face as business leaders - but a single “extinction level event” like having your bank account compromised and all of your company cash balance or investor capital disappear - is suddenly a much greater threat than it has ever been before.
I urge you to take another look at the risks you identified 12 months ago and ask yourself, is any one of these an extinction-level event, and has the landscape changed enough to make our mitigations ineffective?
Thanks for reading and I hope this helps secure you against identity theft and bank account compromise, and gives your investors confidence that their capital is safe.
SK